Security expert Craig Heffner from Seismic, a company specializing in security consulting, will be sharing the details of a security flaw that opens up many common household routers to a hack. The revelation will be part of the Black Hat Conference in Las Vegas at the end of the month. Black Hat is a gathering of technologists who are interested in security issues, some from the corporate world and some from the darker side of the issue. Heffner’s talk is entitled How to Hack Millions of Routers.â€
According to Forbes, Heffner will release code that can be used to get into popular routers from Linksys, Dell, and Verizon FIOS or DSL. If a user visits a web site with the code, malicious hosts can gain access to information or send a browser to another site.
The way the hack works is extremely technical. If you want all the details check out the Forbes blog post. Simply put, it exploits the way Domain Name Systems (DNS) work. The DNS address is kind of like a web page’s phone number. When you type in Notebooks.com a request is sent to a computer connected to the Internet called a DNS server. It looks up the address Notebooks.com. The DNS server then gives the browser the right Internet Protocol address (IP address) so that it can find the actual computer containing the site’s web pages. An IP address is a series of four numbers ranging from 1 to 255. For example, where I live in NC Google’s IP address is 74.125.47.105. It changes based on your locality.
Each web site can have more than one IP address. The trick is fool the router into giving up its address as if it were the secondary IP address for that site. Then the malicious code hidden in the site can gather access from the router like your login information as if your local network were part of that site. Forbes says this isn’t new, but has been patched repeatedly. However, Heffner has found a new way to exploit the system to gain access to most of the popular consumer routers. One of those that is vulnerable is the popular Linksys WRT54G routers.
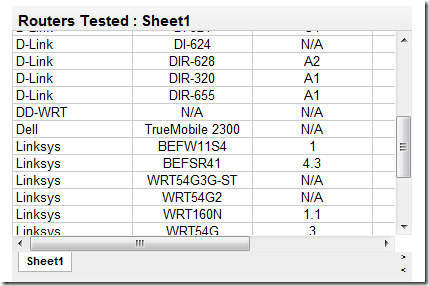
You should go to the Forbes site and find out if your router has been tested. Towards the end of the post is a table listing some of the routers tested with for the vulnerability.
To secure your router do the following:
- Change your password to a strong one. You do this by logging into the configuration page of your router, usually something like 192.168.1.1. Get specific instructions from your manufacturer’s website. Here is a site that will generate very strong passwords for you. The length should be set to at least 8 characters and include letters (both upper and lower case), numbers, and maybe even punctuation marks. Do not include words or names.
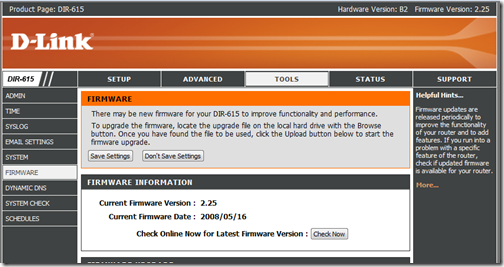
- Go to your router’s support site and get the latest firmware and install it. This is different for each router. Some routers have a link in the router’s configuration page (see below).
- Be careful which web sites you visit. Porn and pirated software pages are notorious for including this kind of code.
“One comfort for users may be that Heffner’s method still requires the attacker to compromise the victim’s router after gaining access to his or her network. But that can be accomplished by using a vulnerability in the device’s software or by simply trying the default login password. Only a tiny fraction of users actually change their router’s login settings, says Heffner. ‘Routers are usually poorly configured and have vulnerabilities,” he says. “So the trick isn’t how to exploit the router. It’s how to get access to it.'” (Andy Greenberg, Forbes)
Some may ask why would Heffner reveal this information? He believes it is the best way to force companies to update their software. As you notice from my router above, D-Link has not updated the firmware in a long time. Fortunately, most D-Link routers are not on the list of vulnerable routers.
The source for this was Dwight Silverman of the Houston Chronicle.