Last week we told you about the Flashback Trojan that infected about one percent of all Mac OS X systems and showed you how to remove it, but there’s now an easier way to check.
The malware hit 450,000 Macs. That’s one percent of the 45 Million Macs worldwide. While Flashback infected a relatively small number of systems, you don’t want your system counted among them. You can follow our instructions for checking to see if you’re infected and then get rid of the threat. If you don’t mind running a script downloaded from the web, then we discovered an easier way to find out if the trojan infected your Mac.
You can run the Flashback checker, a script created by a person with the handle “jills” over at github. This simplifies the process, especially for those who don’t understand running commands in the Terminal app on a Mac.
Download the script, which runs on any Mac running OS X 10.5 and above using either a PowerPC or Intel based Mac. The script won’t remove the malware. For that you still have to run the commands from the link above to the How To Remove Flashback guide we posted before. At least you have a quick and simple way to check your Mac thanks to this script found by Ars Technica.
How to Check Using the Script
I downloaded the ZIP file (direct link) and double clicked it to unzip the file in Finder. I then ran the script by double clicking it.
Look for the line that says, “No Signs of infection were found.”
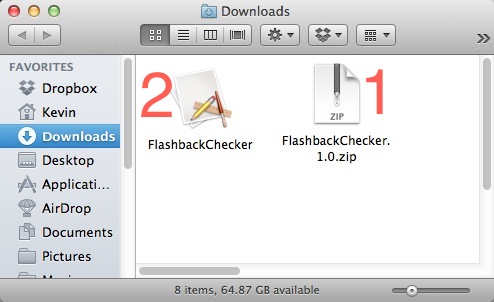
#1 Above is the Zip file. Double Click it to unzip the #2 file above. Double click #2 to run the script.
The script asks if you really want to run it. Give it the OK and it will show you the box below.
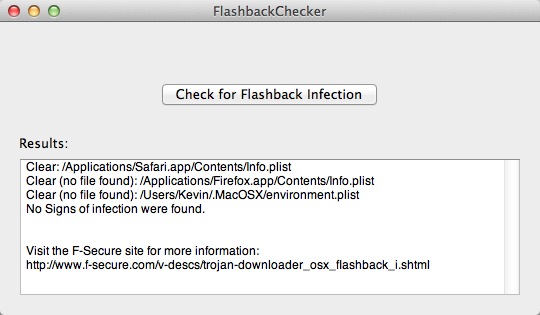
Click the button that says Check for Flashback Infection and it almost instantly finds out if you’re infected. It will give you a link to the F-Secure site that has the removal instructions. I pasted them below for your convenience.
Be sure to get some malware defense in the form of one of the apps we recommended.
Infection Removal Instructions
Manual Removal
Caution: Manual disinfection is a risky process; it is recommended only for advanced users. Otherwise, please seek professional technical assistance. F-Secure customers may also contact our Support.Manual Removal Instructions
1. Run the following command in Terminal:
defaults read /Applications/Safari.app/Contents/Info LSEnvironment
2. Take note of the value, DYLD_INSERT_LIBRARIES3. Proceed to step 8 if you got the following error message:
“The domain/default pair of (/Applications/Safari.app/Contents/Info, LSEnvironment) does not exist”
4. Otherwise, run the following command in Terminal:
grep -a -o ‘__ldpath__[ -~]*’ %path_obtained_in_step2%
5. Take note of the value after “__ldpath__”6. Run the following commands in Terminal (first make sure there is only one entry, from step 2):
sudo defaults delete /Applications/Safari.app/Contents/Info LSEnvironment
sudo chmod 644 /Applications/Safari.app/Contents/Info.plist
7. Delete the files obtained in steps 2 and 58. Run the following command in Terminal:
defaults read ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
9. Take note of the result. Your system is already clean of this variant if you got an error message similar to the following:
“The domain/default pair of (/Users/joe/.MacOSX/environment, DYLD_INSERT_LIBRARIES) does not exist”
10. Otherwise, run the following command in Terminal:
grep -a -o ‘__ldpath__[ -~]*’ %path_obtained_in_step9%
11. Take note of the value after “__ldpath__”12. Run the following commands in Terminal:
defaults delete ~/.MacOSX/environment DYLD_INSERT_LIBRARIES
launchctl unsetenv DYLD_INSERT_LIBRARIES
13. Finally, delete the files obtained in steps 9 and 11.
Once you follow these steps, that should clean your system!